Fully Managed Network Security
Networks contain and provide access to a company’s information and assets, allow employees and partners to efficiently share and communicate from wherever business is conducted, and ensure the IT security of valuable data at all times.
Businesses today are built on scalable and efficient networks – whether LAN, WAN or cloud-based – capable of handling the constant evolution of professional practices, new hardware, wireless and mobile devices that a company’s people relies upon. And beyond that, these systems are optimized to suit the particular needs of the business.
From onsite and cloud servers, IT security and software applications to the protocols and policies in place to manage them, the network security strategy and infrastructure will determine the overall potential and performance of the business it serves.
Maintaining Peak Network Security Performance
Supra ITS provides the strategy, systems, processes and support that protect business’s IT infrastructure and ensure maximum uptime and performance. Managed Network Security Services are at the heart of our Managed Services portfolio. They help create the technological foundation of our clients’ businesses; they ensure organizational continuity while maximizing uptime and performance; and they increase productivity. Managed networks and security systems also reduce downtime and costs to create easily measurable ROI and business value.
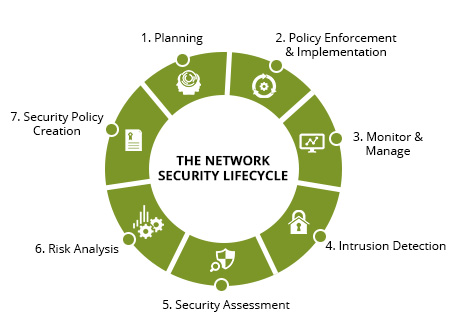
Getting Network Security Strategy Right
As the core technology infrastructure of most modern businesses, networks need to be planned with an intimate understanding of the company and its requirements. Effective networks and security strategies are implemented with seamless expertise and precision, and are managed, supported and maintained by experienced and skilled professionals. Delivering this and more, Supra ITS works with you to provide:
- Adherence to your compliance needs
- Analytics
- Design, implementation and consultation
- Network and deployment plan
- Onsite direction and leadership
- Round-the-clock remote support
- Firewall IDS/IPS
Information and network security strategies are only as good as their latest update, with the constant creation and proliferation of new threats to business’s technology and data revealing themselves daily. A managed firewall protects a business’s data and assets, providing the right people with seamless access while preventing unauthorized parties from trespassing.
Supra ITS’s firewall IDS/IPS support and managed services suite delivers stable, secure and efficient network security, creating a solid foundation on which your business can thrive. Managed Network Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are the best defence against vulnerability and cyber-attacks, with the responsibility of providing the most robust and recent protection resting with dedicated experts using the latest technologies.
Supra ITS provides a complete IDS/IPS solution that relieves internal resources of a near-impossible task of constant monitoring and threat-response. Our security and monitoring teams are available round-the-clock to ensure the best possible protection and response time to verified threats, and work with customers to ensure the best security strategy is in place and appropriate recommendations and upgrades are made before they’re needed.
Our IDS/IPS key features include:
- Auditable and accurate change management
- Backup and recovery
- Device provisioning & deployment
- Device upgrades
- Flexible management options
- Performance and availability management
- Threat monitoring and response
- Scheduled or on-demand security and compliance reports
- Let your business feel the Managed Network Security benefits
- On-time security updates reduce network vulnerability
- Firewall layered configuration fits your organization and user needs
- 24/7 Firewall support minimizes downtime
- Managed firewall service saves your in-house IT resources time
- Remote monitoring service and reports deliver proactive security measures
We work together to assess your network environment and operational needs to define technical parameters and goals, then design and implement the necessary security protocols to provide greater control over network devices and users, while retaining the optimal access and usability.
By minimizing risk, using best practices, applied security technologies and a philosophy of continuous improvement, your network’s days of performance anxiety are over.




 Latest Blogs
Latest Blogs FAQ
FAQ